The SOC of the Future: Scale your Security at Speed
Oct 19, 2022 1:44:13 PM | Digital Hands
The concept of a Security Operations Center (SOC) was born in the 1990s among large global enterprises. While the very first security operation centers were created to centralize expertise focused on detection and response1, today's definition of a SOC is much more broad and ambiguous.
Generally speaking, a SOC is a centralized command unified around three key pillars: people, processes, and technology. As businesses adopt new technologies in pursuit of enhancing their processes and achieving critical business goals, we've seen more data, security blind spots, and vulnerabilities than ever before. This is prompting experts to question if this "Big Data" issue can be addressed by hiring more talent or enabling automation capability instead.
Cybersecurity Workforce Challenges
According to the 2023 (ISC)² Cybersecurity Workforce Study, there's a global cybersecurity workforce gap of 3.4 million people and experts estimate that the global cybersecurity workforce needs to grow by 65% to defend critical assets in companies effectively. Despite millions of open positions currently in the cybersecurity industry, efforts to close this gap have not made any significant impact.
To build a SOC you will typically need at least 8 security analysts. Ramping up a team of 8 while trying to avoid churn due to the competitive nature of the cybersecurity industry is indeed a challenge.
Due to the rapid shift of security infrastructures, operating modes, and evolving threat actors, finding cybersecurity talent with the right knowledge and skills can be difficult. Moreover, if you do manage to source effective talent, your SOC will still have to come up with processes to overcome traditional SOC challenges.
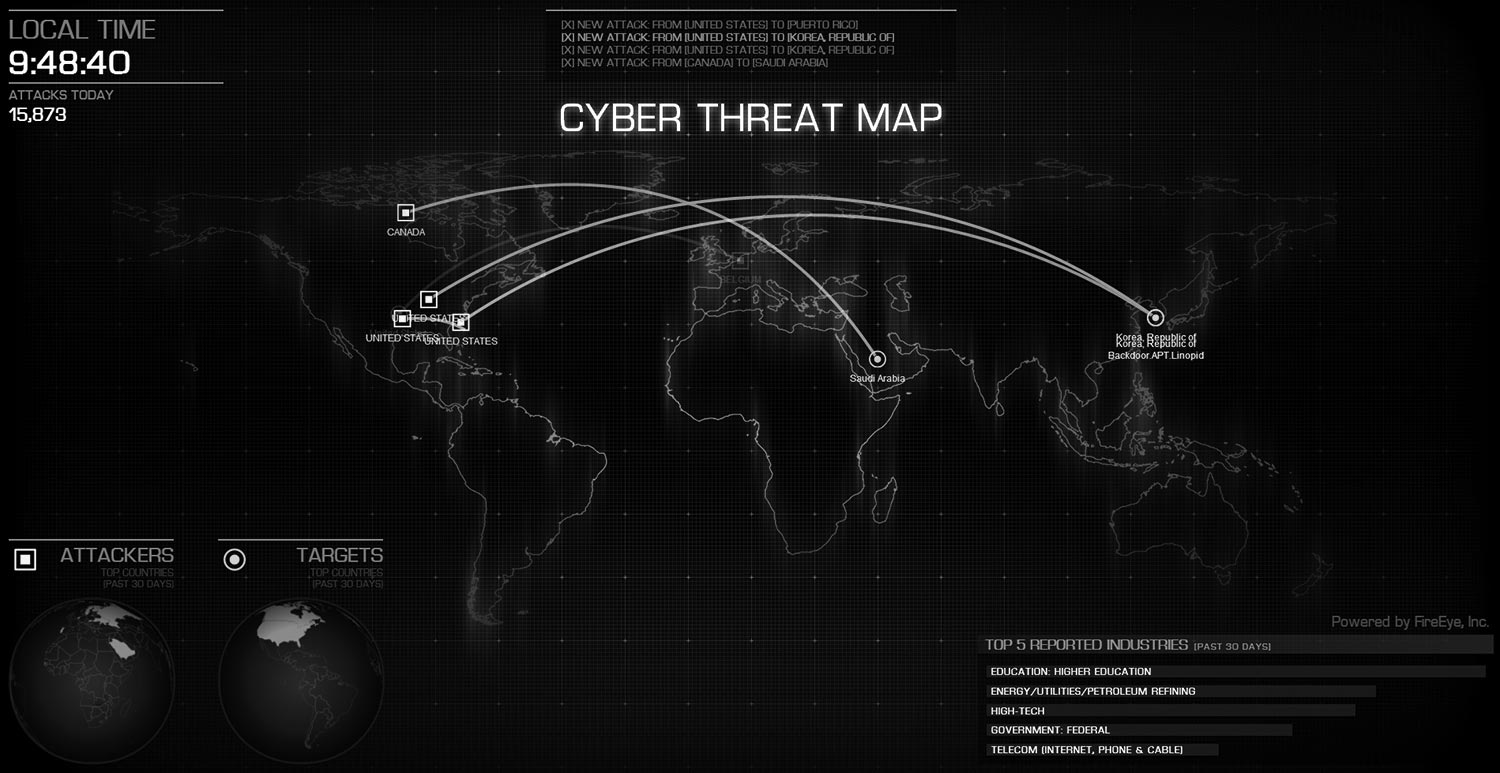
Fatigue from high rates of false positives, BIG data, and endless alerts are common issues of a traditional SOC. The sheer amount of data generated by today's technologies and landscape makes it difficult for your SOC to quickly prioritize and remediate threats.
Introducing the SOC of the Future
A new model is needed to combat the cybersecurity talent shortage, a profound increase in attack surfaces, and the sophistication of threats. Organizations must move towards achieving a "SOC of the Future".
The SOC of the Future framework is built around the idea that security operations activities must effectively scale with the swift expansion and evolution of people, processes, and technologies, while leveraging autonomic functions to combat modern threats at speed3.
This automation-centric strategy creates scalable and provable outcomes, solving security problems without incurring exponential costs that would occur from trying to source more talent4.
Your security analysts will need automation, integrations, and the latest threat intelligence at their fingertips. The expertise of your security team is invaluable but so is the tech stack you arm them with. Threat Intelligence can run at a cost of $120K a year.
A SOC of the future needs to adopt both cloud-based and on-premise architecture to truly be ready for anything and be able to deliver composable security solutions.
Speed and scale are key and so you need to make sure your SOC is using a SIEM that is able to ingest data at lightning speed while enabling your analysts to make decisions at machine speed.
Working with the right Managed Security Service Provider (MSSP) ensures that you not only have access to 24x7x365 veteran security operations experts but also peace of mind knowing that you're utilizing continuously-vetted and industry-leading technologies necessary to get ahead of every threat.
Digital Hands CyGuard Maestro™ Detects Faster to Respond Faster
Achieve a SOC of the Future with Digital Hands
All of our CyGuard® services will provide your organization access to CyGuard Maestro™'s powerful automation, our premium multi-source Harbinger Threat Intelligence feed, and our veteran US-Based SOCs.
If your team is in need of achieving security compliance or is looking to implement or manage a SIEM solution, Digital Hands can help.
1, 3, 4 Autonomic Security Operations; Google Cloud
2 2023 (ISC)2 Workforce Study; (ISC)2
We're here to help
Table of Contents
Subscribe to Our Monthly Newsletter
The latest on emerging threats and strategies—straight to your inbox.
By submitting this form, you agree to Digital Hands' Terms of Use and Privacy Policy.
Subscribe to Our Monthly Newsletter
The latest on emerging threats and strategies—straight to your inbox.
By submitting this form, you agree to Digital Hands' Terms of Use and Privacy Policy.